The following steps are required to forward Palo Alto logs to Cyfin Syslog Server:
- Create a syslog server profile.
- Configure a log forwarding profile to select the logs to be forwarded to Cyfin Syslog Server.
- Assign the log forwarding profile to security rules.
The logs that must be forwarded are the Threat logs with Informational severity. Informational Threat logs include URL Filtering, Data Filtering, and WildFire logs.
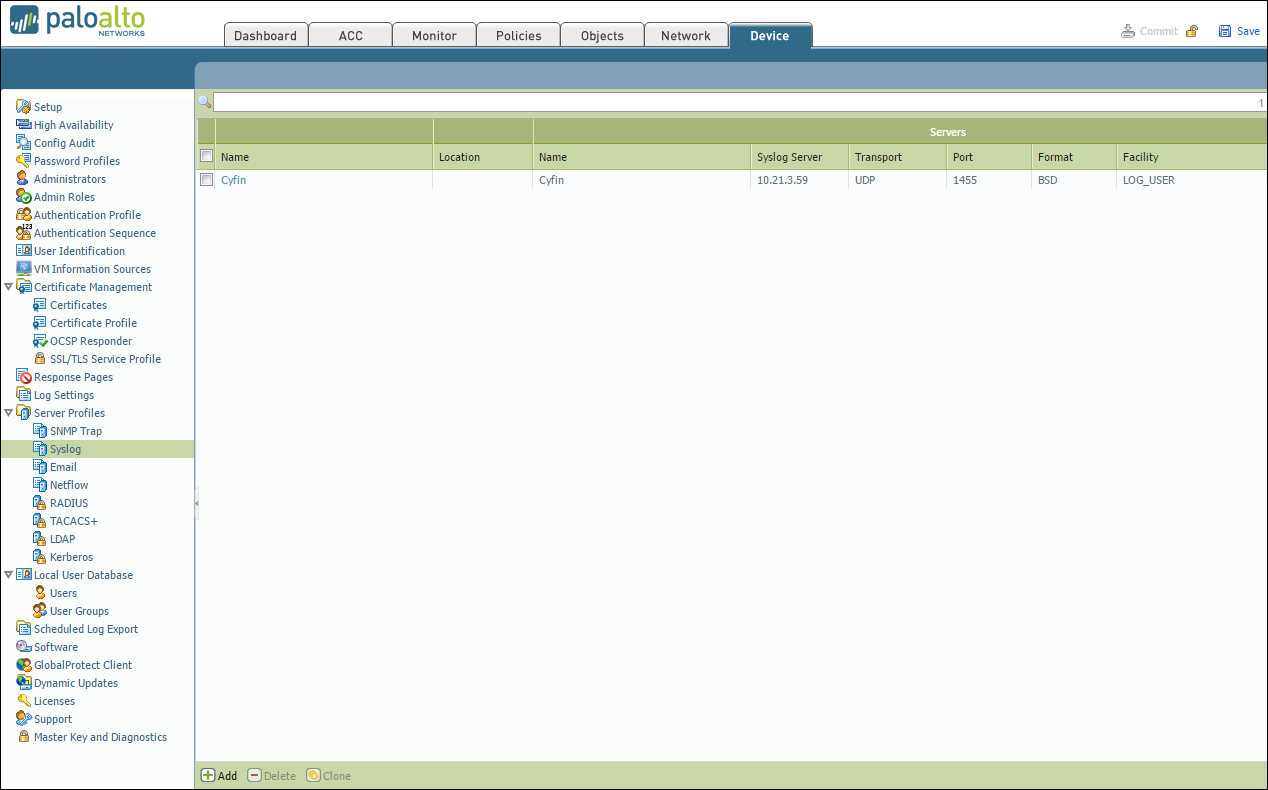
Syslog Server Profile
- In your Palo Alto Firewall user interface, go to Device – Server Profiles – Syslog.
- Click Add at the bottom of the screen.
- Enter the following information:
- Name – Cyfin
- Syslog Server – IP address of where Cyfin is installed
- Transport – UDP
- Port – 1455
- Format – BSD
- Facility – LOG_USER
- Click OK to save the server profile.
- Click Commit at the top of the screen to commit the change.
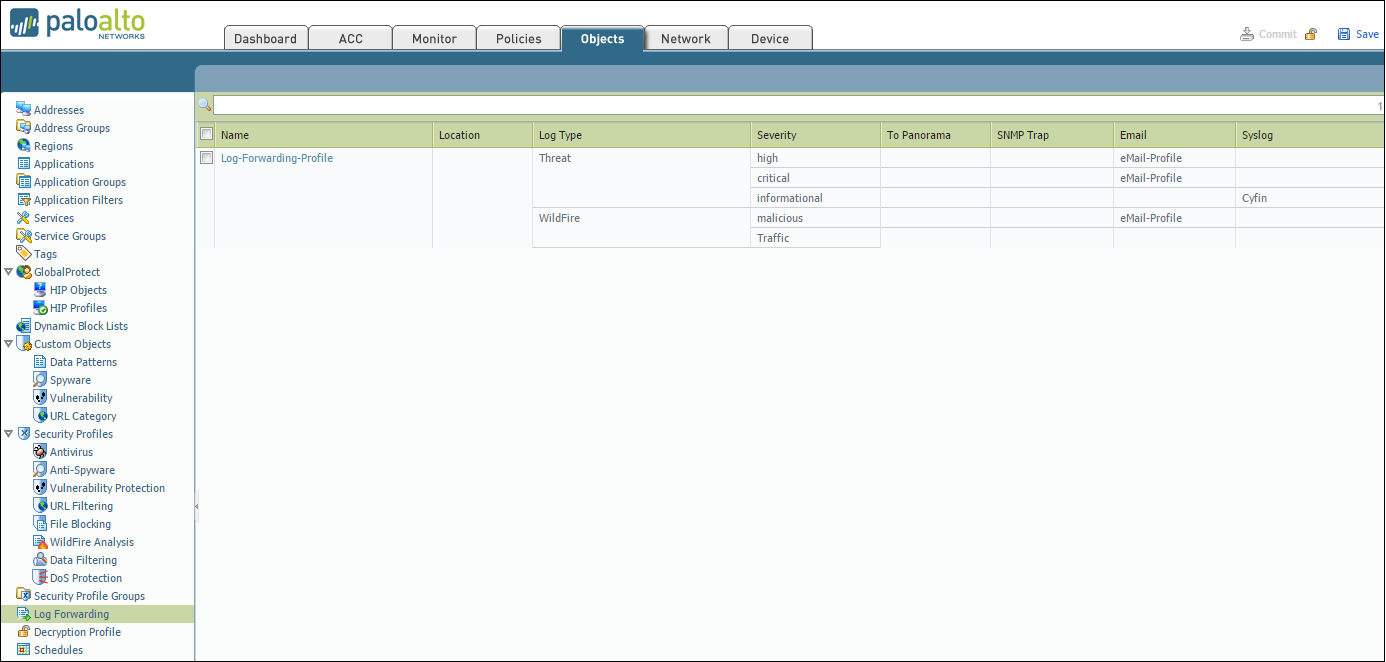
Log Forwarding Profile
- Go to Objects – Log Forwarding.
- Select the syslog server profile (Log-Forwarding-Profile) for forwarding Threat logs to Cyfin.
- In the Threat drop-down field, ensure that for the Severity Informational option, Cyfin is selected in the Syslog column.
- To forward URL Filtering logs, add Log Type “URL” and set Severity to “Informational.” Then set Syslog to “Cyfin.”
- To forward Traffic logs, add Log Type “Traffic” and set Severity to “Informational.” Then set Syslog to “Cyfin.”
- Click Commit at the top of the screen to commit the change.
URL Filtering Profile
To log the traffic from URL Filtering logs, you may need to adjust the Site Access for each allowed URL category.
- Go to Objects – URL Filtering – URL Filtering Profile.
- Select Categories – Site Access.
- Filter by “Allow.”
- Change “Allow” to “Alert” for each category listed.
Security Policy Rule
- Go to Policies – Security.
- Select the rule for which the log forwarding needs to be applied.
- Apply the security profile to the rule.
- Go to Actions and in the Log Forwarding drop-down field, select the log forwarding profile.
- Click OK. By default, when Threat logs are forwarded to Cyfin Syslog Server, the logs will have several fields including source IP address, destination IP address, and URL.
- Click Commit at the top of the screen to commit the change.
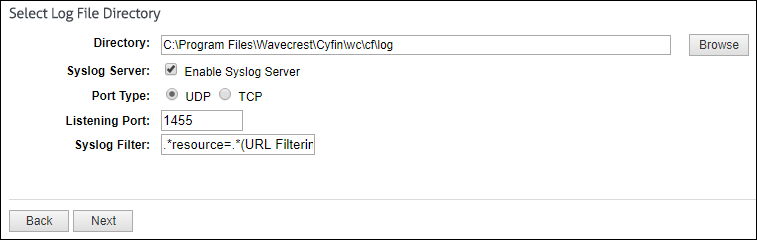
Now, you can configure Cyfin to write the forwarded Palo Alto log files to syslogYYYYXXXX.txt files. See Cyfin Configurations Steps for more information.
Additional Resources:
- Palo Alto Firewall Syslog Setup from Palo Alto Customer Support: Video Tutorial
- Wavecrest video on setting up Cyfin Syslog: Cyfin Syslog Setup Video
- Palo Alto Customer Service Syslog guide: PA Tips and Tricks Link