The following steps pertain to Cisco Firepower Threat Defense and are required to forward these logs to Cyfin Syslog Server:
- Select Devices – Platform Settings and create or edit a Firepower Threat Defense policy.
- Select Syslog – Syslog Server.
- Check the Allow user traffic to pass when TCP syslog server is down check box to allow traffic if any syslog server that is using the TCP protocol is down.
- Enter a size of the queue for storing syslog messages on the security appliance when syslog server is busy in the Message queue size (messages) field. The minimum is 1 message. The default is 512. Specify 0 to allow an unlimited number of messages to be queued (subject to available block memory).
- Click Add to add a new syslog server.
- In the IP Address drop-down list, select a network host object that contains the IP address of the syslog server.
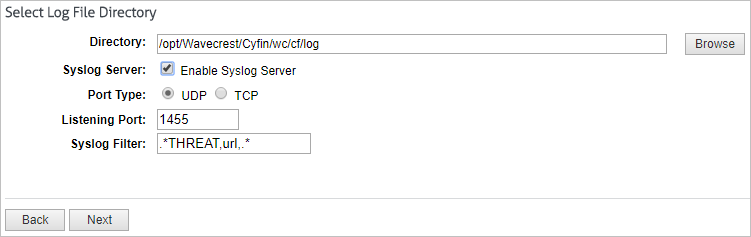
- Choose the protocol (either TCP or UDP) and enter the port number for communications between the Firepower Threat Defense device and Cyfin syslog server.
- The default ports are 514 for UDP and 1470 for TCP. Valid nondefault port values for either protocol are 1025 through 65535.
- Check the Log messages in Cisco EMBLEM format (UDP only) check box to specify whether to log messages in Cisco EMBLEM format (available only if UDP is selected as the protocol).
- Add the zones that contain the interfaces used to communicate with the syslog server. For interfaces not in a zone, you can type the interface name into the field below the Selected Zones/Interface list and click Add. These rules will be applied to a device only if the device includes the selected interfaces or zones.
Note: If the syslog server is on the network attached to the physical Management interface, you must type the name of that interface into the Interface Name field below the Selected Security Zones list and click Add. You must also configure this name (if not already configured), and an IP address, for the Diagnostic interface (edit the device from the Device Management page and select the Interfaces tab).
- Click OK.
- Click Save.
You can now click Deploy and deploy the policy to assigned devices. The changes are not active until you deploy them.
Click here for more information from Cisco.
Additional Resources
- Wavecrest video on setting up Cyfin Syslog: Cyfin Syslog setup video