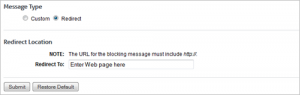
To get Group Policy support for Firefox, you can load the ADM files. FirefoxADM is a way of allowing centrally managed, locked and/or default settings in Firefox via Group Policy and Administrative Templates in Active Directory. Although Firefox does not support GPOs natively, this open source ADM file will allow automatic configuration through GPO.
Downloading the ADM files
You can download and extract the latest files, including detailed documentation, at http://sourceforge.net/projects/firefoxadm.
Turning on Group Policy
- On the Active Directory server, open Group Policy Management by going to Start – All Programs – Administrative Tools.
- Right-click the group to which you would like to add this GPO and click Create a GPO in this domain, and Link it here…
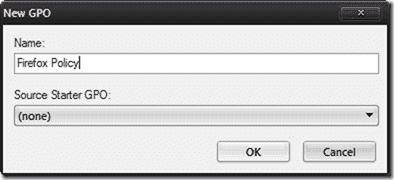
- Enter a descriptive name for the policy and click OK.
- Right-click the newly created policy and click Edit. This will open the Group Policy Management Editor.
- Expand User Configuration – Policies and right-click Administrative Templates. Select Add/Remove Templates…, click Add… on the dialog box, and then browse to where you extracted the FirefoxADM files. You will notice that there are two ADM files–firefoxdefaults.adm and firefoxlock.adm.
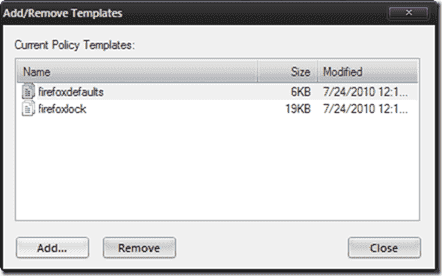
- Select both of them, and click Open and then Close after the files have been imported.
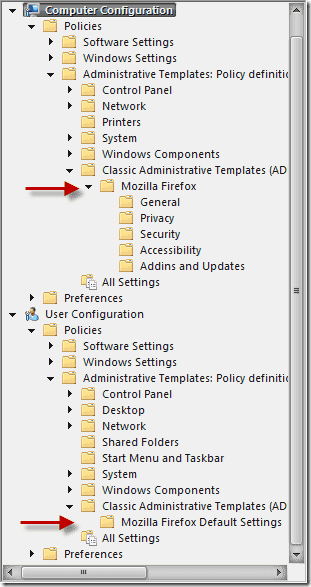
- Notice that the Firefox settings are under User Configuration – Policies – Administrative Templates – Classic Administrative Templates, as well as under Computer Configuration – Policies – Administrative Templates – Classic Administrative Templates, and that they are not the same.
As their locations in the tree suggest, the computer configuration will configure all defaults for Firefox on a machine in the group. The user configuration is user specific.
How FirefoxADM overcomes the lack of native support is addressed next. When you extracted the zip file, you should have noticed some extra VBS files, specifically firefox_login.vbs, firefox_logout.vbs, firefox_shutdown.vbs, and firefox_startup.vbs.
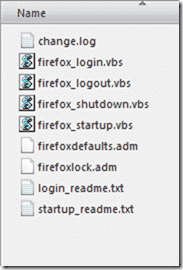
- To make these configuration changes, VB scripts are used to configure Firefox during logon, logoff, startup, and shutdown. These scripts should be imported to their correct locations inside the policy.
- In Group Policy Management Editor, navigate to Computer Configuration – Policies – Windows Settings and select Scripts (Startup/Shutdown).
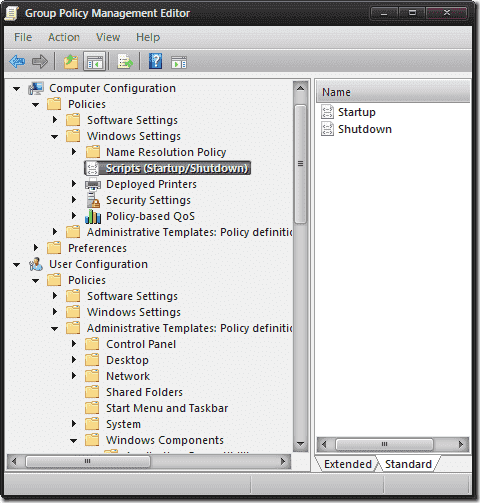
- Double-click Startup in the right pane. A Startup Properties box will appear. Click the Add… button on the right.

- An Add a Script box will appear. Click the Browse… button, locate the firefox_startup.vbs file you extracted earlier, and double-click it. Click OK to close the box.
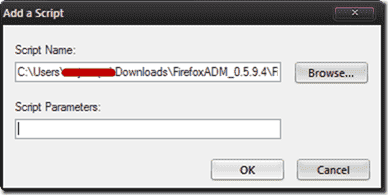
- Click the OK button again to close the Startup Properties box. Repeat the steps above for the Shutdown script.
- Next, navigate to User Configuration – Policies – Windows Settings and select Scripts (Logon/Logoff). Then repeat the same steps as above pairing Logon with firefox_login.vbs and Logoff with firefox_logout.vbs.
- You have just configured GPO for Firefox. Now those scripts will run when the computer is started and shut down when a user logs on and logs off.
Note: Wavecrest Computing is providing this for informational purposes only. Please use at your own discretion.