With your firewalls already forwarding logs to Panorama, the high-level steps to forward Palo Alto Panorama logs to Cyfin Syslog Server include the following:
- Configure the server profile that defines how Panorama and Log Collectors connect to the external service, that is, Cyfin Syslog Server.
- Assign the server profile to the log settings of Panorama and to Collector Groups.
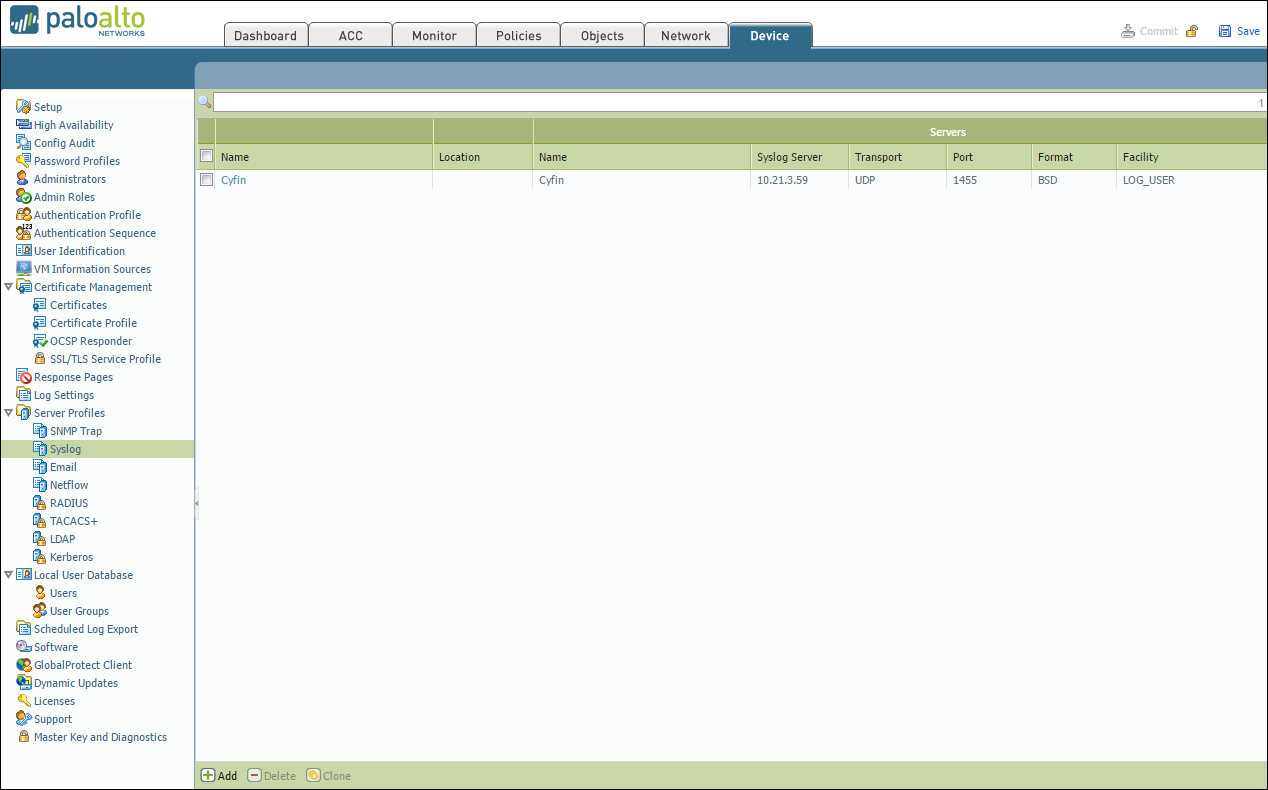
STEP 1: Configure a server profile for Cyfin Syslog Server that will receive log information.
- Select Panorama – Server Profiles and select Syslog.
- Configure the syslog server profile.
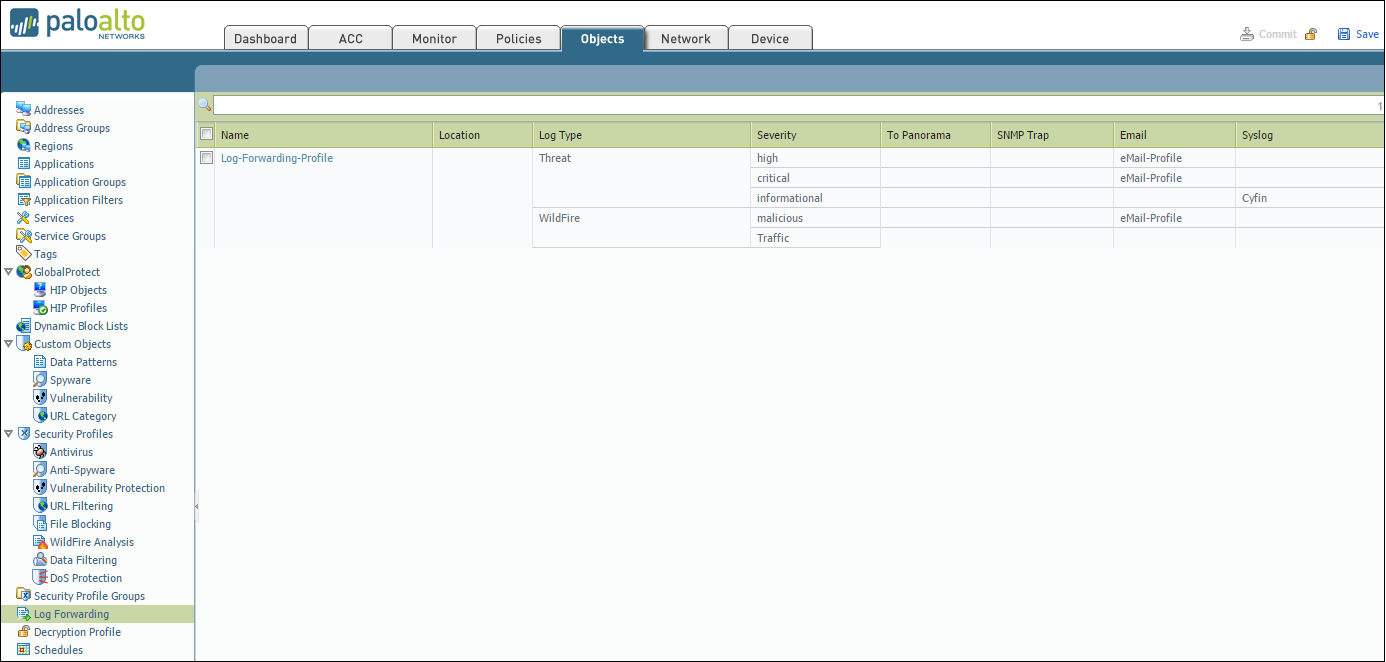
STEP 2: Configure destinations for:
- Logs that the Panorama management server and Log Collectors generate.
- Firewall logs that a Panorama virtual appliance in Legacy mode collects.
- Select Panorama – Log Settings.
- Add one or more match list profiles for each log type.
The profiles specify log query filters, forwarding destinations, and automatic actions such as tagging. For each match list profile:
-
- Enter a Name to identify the profile.
- Select the Log Type.
- In the Filter drop-down field, select Filter Builder. Specify the following and then Add each query:
- Connector logic (and/or)
- Log Attribute
- Operator to define inclusion or exclusion logic
- Attribute Value for the query to match
- Add the server profile you configured for Cyfin Syslog Server.
- Click OK to save the profile.
STEP 3: Configure destinations for firewall logs that Log Collectors receive.
- Select Panorama – Collector Groups and edit the Collector Group that receives the firewall logs.
- Select Collector Log Forwarding and see step Add one or more match list profiles for each log type above.
- Click OK to save your changes to the Collector Group.
STEP 4: Commit and verify your configuration changes.
- Select Commit – Commit and Push to commit your changes to Panorama and push the changes to device groups, templates, and Collector Groups.
- Verify that Cyfin Syslog Server is receiving the log information in one of the following ways:
- In the log folder, check for the syslog.txt file.
- In Cyfin, go to Data Management – Log Data Source – Viewer to check for syslog.txt.
Additional Resources:
- Updated steps from Palo Alto: Configure Log Forwarding Panorama
- Wavecrest video on setting up Cyfin Syslog: Cyfin Syslog setup video