In Cyfin version 9.3.1, the Log Data Source Setup wizard has been redesigned to improve the configuration of the product to locate and read your Web-use data when it is syslog data, log files, or database logs. The system will analyze your data to detect the data source format and present the most suitable data types. This allows you to select the best data type from the list and ensures that you get the best match available.
You will be able to select from the following data sources: syslog, directory-based, and database.

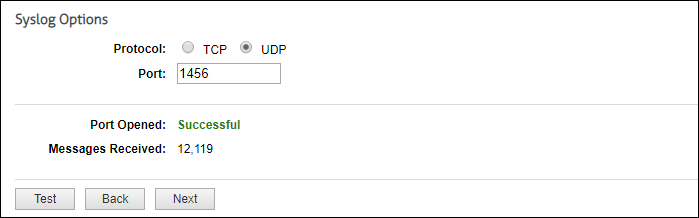
For syslog data, select the Internet protocol you want to use, and enter the listening port number. Click Test to start collecting data. If this is successful, you will see the number of messages received incrementing. Click Stop and then Next to continue.
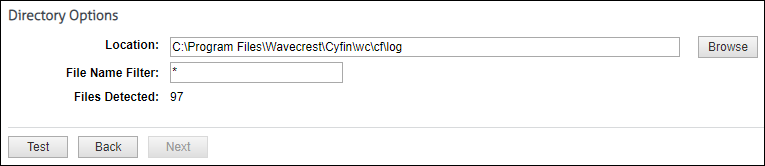
For directory-based or log file data, specify the directory location of your data files. You can also enter a file name with an asterisk to filter your log files, e.g., proxy*.txt. Click Test to display the number of files found. Click Next.
The Data Source Type page is displayed.
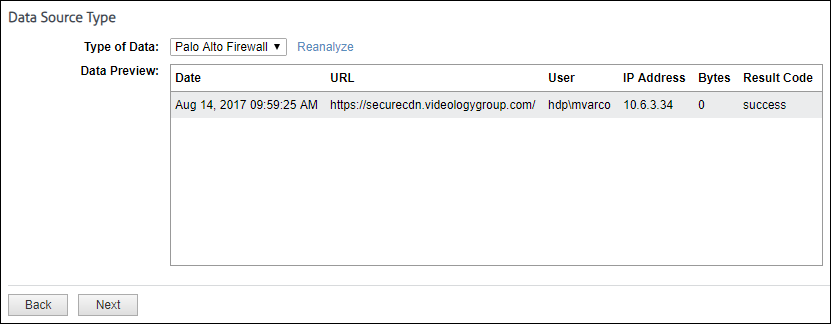
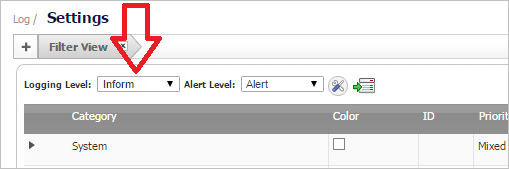
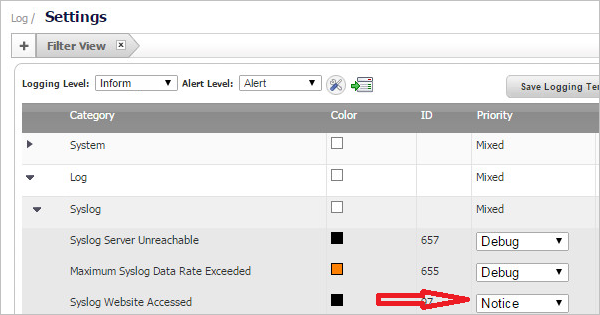
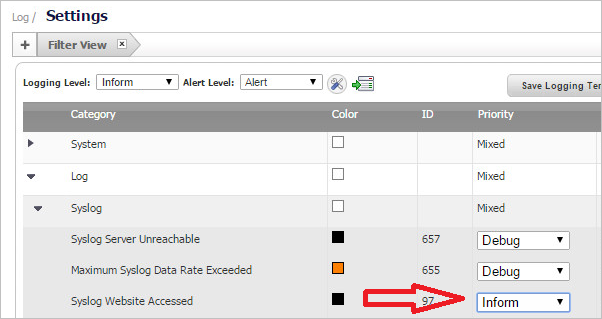
The Type of Data drop-down field will display multiple matches. As you select a data type, the data format will be shown in the Data Preview box. Look closely at the data fields to ensure that they are correct or complete.
- You may see incomplete data, for example, if you were expecting a user name and it is missing. Click Reanalyze to see another record sample.
- If you need to refresh the data for any reason or are still in the process of receiving syslog messages, click Reanalyze and then select the data source type again.
- If your firewall is not in the drop-down field, but the data of another completely matches and is in the correct columns, you may select that firewall even though it has a different name. Some firewalls share common data formats.
- If no matches are found, all syslog and directory data types will become available in the drop-down field. You can select a different data type from the field to complete the configuration process and return at a later time to change it.
- It is easy to add new data sources to our extensive library. If you have a new data source, need assistance with multiple matches, or have no matching files, just contact Technical Support.
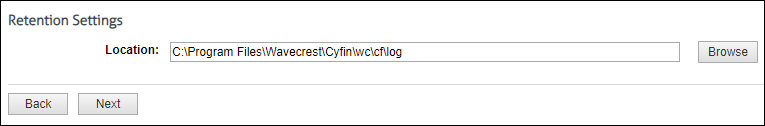
Also for Syslog, you can specify a location in which to keep a local copy of your data.
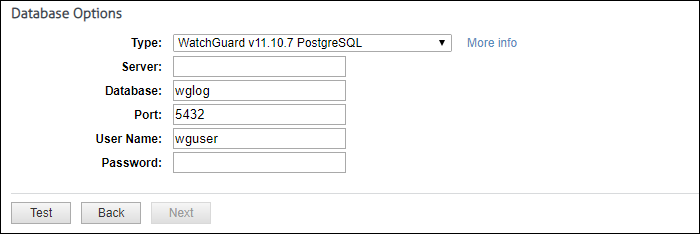
For database data, the system loads and populates the Type field with database data types. The “More info” link provides setup information on your specific database. Select the type of database and complete the remaining fields. Some fields will be populated with default values.
The last step is to give the data source configuration a name. This is helpful for identification purposes, especially if you add more data source configurations later.
If you have any questions, please contact Technical Support at (321) 953-5351, Ext. 4 or support@wavecrest.net.